In a world where digital collaboration shapes business success, APIs stand as the unsung heroes. But what happens when these vital channels become targets for cyber threats? Discover how unsecured APIs can be the Achilles’ heel of your digital strategy and learn how to fortify them against emerging cyber dangers.
As we delve deeper into the complexities of API management, it’s essential to start with the fundamentals. A key aspect of this is understanding the basic concept of API security. So, what exactly is API security?
What is API Security?
API security is a crucial aspect of web application and application security, involves protecting application programming interfaces (APIs) against vulnerabilities such as SQL injection, DDoS attacks, and broken object-level authorization. This practice is essential for maintaining the integrity and confidentiality of sensitive data transferred via API calls. Effective API security incorporates strategies like robust authentication, rate limiting, and encryption (SSL/TLS) to safeguard against security risks.
APIs, serving as gateways for data exchange in apps, IoT devices, and microservices, require vigilant access control measures like OAuth and validation of API requests. Regular security testing, adherence to OWASP API security top 10, and deploying measures like WAF (Web Application Firewall) and API gateways are pivotal in preventing data breaches and securing API endpoints.
As we delve deeper into API security best practices, we’ll explore how to secure REST APIs, manage API traffic, and address security vulnerabilities, ensuring protection against types of attacks including excessive data exposure, scripting, and automated threats. Understanding API security is crucial for developers, security teams, and providers in the evolving landscape of API management and DevOps.
Why Is API Security Important?
API security is crucial because APIs are the backbone of modern digital communication between applications, enabling data exchange and functionality sharing. APIs, often publicly accessible, are prime targets for attacks such as denial of service (DoS), distributed denial of service (DDoS), and mass assignment vulnerabilities. Effective API security protects the backend systems and sensitive data from unauthorized access and misuse. It ensures data integrity and reliability of services, preventing disruptions that can result from attacks. By implementing measures like function level authorization, transport layer security (TLS), and API protection strategies, organizations can safeguard their digital assets and maintain trust with their users.
How is API Security Different From General Application Security?
API security differs from general application security in its focus and methods. While application security broadly covers all aspects of safeguarding an application from threats, API security specifically addresses issues at the API level, including the handling of JSON and XML data formats. It involves securing the communication channel, often using protocols like SOAP (Simple Object Access Protocol) and GraphQL, and managing API-specific vulnerabilities. API security also requires managing unique identifiers and keys, ensuring secure authentication and authorization at the API gateway, and addressing specific API threats identified by standards like OWASP Top 10 for API security.
The Top 10 API Threats
The Open Web Application Security Project (OWASP) lists the top 10 API threats that organizations should be aware of to enhance their API security posture. These include:
- Injection Attacks: Malicious code injection through APIs using JSON, XML, or other data formats.
- Broken Authentication: Weaknesses in authentication mechanisms leading to unauthorized access.
- Sensitive Data Exposure: Inadequate protection leading to access to sensitive data.
- XML External Entities (XXE): Attacks targeting poorly configured XML processors.
- Broken Access Control: Failing to restrict access properly at different API endpoints.
- Security Misconfigurations: Common misconfigurations that expose APIs to attacks.
- Mass Assignment: Exploiting APIs by mass assigning data fields not intended for exposure.
- Data Validation Issues: Lack of proper input validation leading to various attacks.
- Improper Assets Management: Inefficient tracking and securing of APIs and endpoints.
Insufficient Logging and Monitoring: Failing to detect and respond to breaches promptly.
Addressing these threats requires a comprehensive approach to API security, encompassing web services security, transport layer security, and consistent monitoring and updating of security measures. To explore more about the top API threats and how to mitigate them, check out What API Security Policies and Rate Limiting.
As we delve deeper into the nuances of API security, it’s important to understand its dual role in facilitating collaboration and posing security risks. The next section will further explore this dynamic in depth.
APIs: The Double-Edged Sword of Collaboration and Security Risks
APIs are key vehicles for organizations to collaborate internally, within departments, and externally, with customers and partners, effectively acting as the backbone of modern web APIs. They also play a pivotal role in application integration, especially with third-party APIs created by partners or public entities. However, a recent survey revealed a significant vulnerability: a large percentage of internal and as much as 25% of third-party APIs are not managed, exposing them to various API security risks and vulnerabilities. This oversight in API management can lead to severe consequences, such as data theft, financial loss, loss of intellectual property, and damage to reputation, as unsecured APIs form a major part of the attack surface for hackers.
Securing your APIs, which involves strategies like implementing robust authentication protocols, rate limiting to manage API traffic, and addressing API vulnerabilities, is actually a relatively straightforward task with the right tools and approaches. SnapLogic API Management solution, integrated with a top-tier iPaaS platform, empowers organizations to effectively manage and govern both internal and external APIs. This post will delve into various security policies offered by the SnapLogic API Management solution, ranging from the more open ‘Anonymous Authenticator’ to the more stringent ‘OAuth2’, and how these can help mitigate security misconfiguration and other security threats.
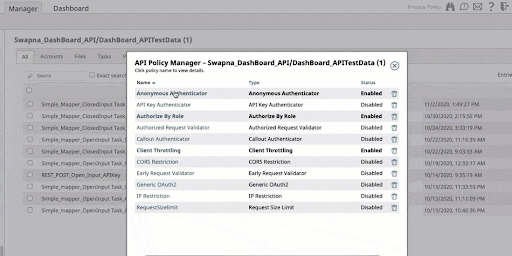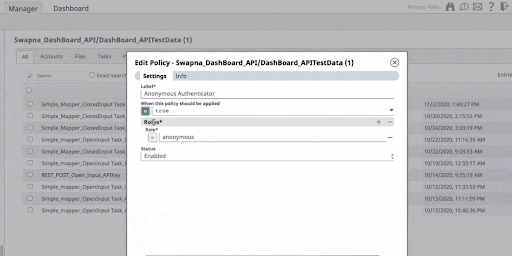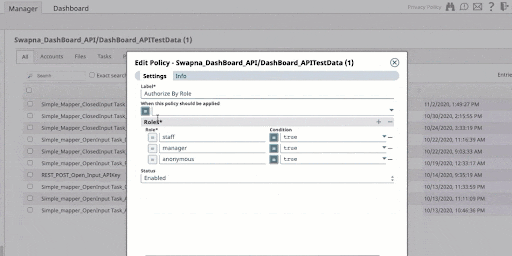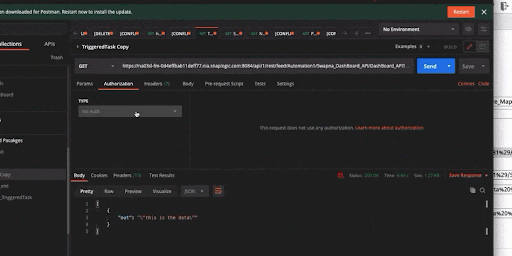
For a detailed overview of the various policy types available for application on the SnapLogic API Gateway, refer to Figure 1 below. Additionally, understanding the importance of the right API gateway architecture in securing APIs, and the benefits of effectively managing API traffic, are crucial in the broader context of API security and management.

SnapLogic API Management Access Control Policies
Here is a list of 12 access control policies that you can use with the SnapLogic API Management solution to ensure robust application security and manage API traffic effectively.
1 – Anonymous Authenticator
The Anonymous Authenticator policy enables open access to your API, which is common for read-only access or public data exposure. This policy is activated when a request is made without a specific authentication method, like OAuth or user authentication. To balance the inherent security risks, it’s recommended to pair it with an authorization policy assigning an ‘anonymous’ role, effectively addressing potential API vulnerabilities. Additionally, integrating this policy with a throttling mechanism is crucial to prevent DDoS attacks and excessive data exposure by controlling the rate of API requests. Monitoring the client’s IP address is also vital for managing access and usage at the API gateway level.
2 – Authorize by Role
The Authorize by Role policy strengthens security by authorizing API requests based on the client’s role, a key aspect of access control. This policy, activated post-authentication, is essential for securing sensitive information and executing functions. It minimizes the attack surface and reduces the risk of security misconfigurations by specifying roles, allowing API creators to finely tune access levels for various parts of the API. This policy is particularly important for managing different types of API calls, such as GET or POST, ensuring that only appropriately authenticated requests access sensitive data or functionalities.
Both Anonyomous Authenticator and Autorize by Role policies are crucial in managing the security of API endpoints within the SnapLogic API Management framework, contributing to a comprehensive strategy for safeguarding sensitive data and applications against various API attacks and security threats. For more insights into implementing a robust API strategy and understanding its value in building a digital ecosystem, read more about APIs and corporate strategy.
3 – API Key Authenticator Policy
The API Key Authenticator policy is a prevalent method for securing APIs, ensuring that clients are authenticated using a unique API key to invoke the API. This key is transmitted either as a header or a query parameter to the API gateway, enhancing security and controlling access. API consumers can manage these keys, including obtaining and renewing them, through the API Developer Portal, which plays a crucial role in maintaining API security and managing API traffic.
4 – Authorized/Early Request Validator Policies
These policies are instrumental in performing generic validation on API requests. The Early Request Validator operates before authentication, and the Authorized Request Validator post-authorization. By validating requests early, these policies help avoid unnecessary pipeline execution costs in case of invalid requests, contributing to efficient API traffic management and reducing the attack surface for potential security threats.
5 – Callout Authenticator Policy
The Callout Authenticator policy offers flexibility for API developers. If there’s an existing REST service for user authentication, the API gateway can authenticate users by calling out to this external service. This multi-layered approach to security is crucial for protecting APIs from various threats, including unauthorized access and security misconfigurations.
Following this section, Figure 3 illustrates the configuration of a Generic OAuth2 policy with GitHub as an OAuth2 provider, demonstrating the practical application of these security policies in a real-world scenario.
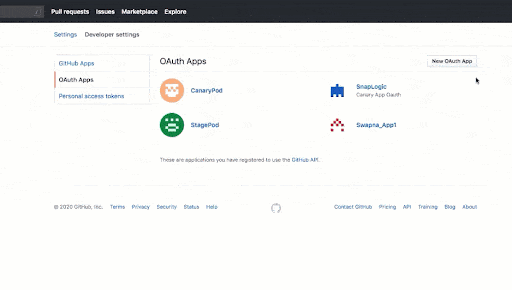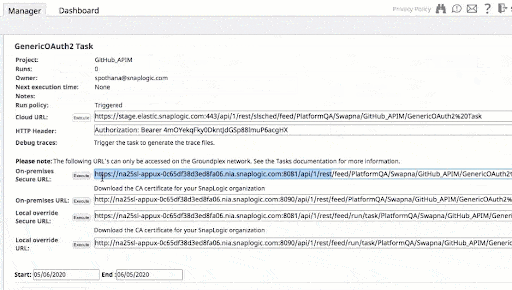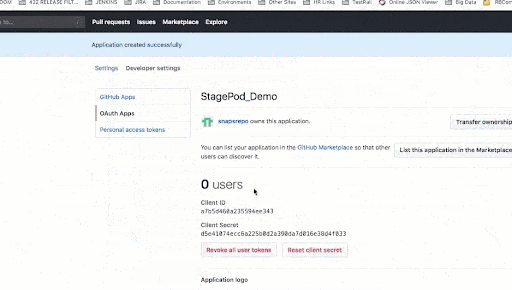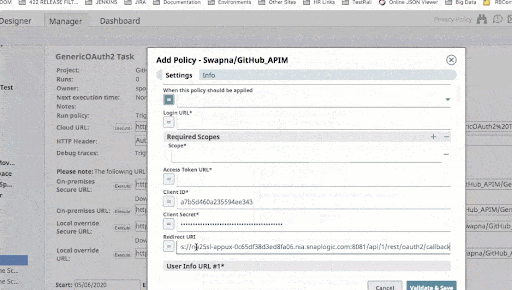
6 – Generic OAuth2 Policy
The Generic OAuth2 policy is increasingly recognized as a standard for robust authentication in the API landscape. It leverages an OAuth2 provider to authenticate clients, redirecting them to complete the authentication flow. Upon receiving the access token, the API gateway obtains an ID and assigned role for the user, ensuring secure, role-based access control and safeguarding sensitive data against unauthorized access.
7 – OAuth2.0 Client Credentials Policy
The OAuth2.0 Client Credentials policy utilizes existing credentials from your OAuth2.0 environment for user authentication. Ideal for machine-to-machine interactions, this policy is pivotal in scenarios where user-level authentication isn’t necessary, thereby reducing the complexity of authentication processes and ensuring the integrity of automated API calls.
8 – IP Restriction Policy
The IP Restriction policy, essential for controlling and monitoring API traffic, restricts access based on the client’s IP address. Particularly useful for internal API usage within an organization, this policy helps mitigate the risk of excessive requests from unauthorized sources, thus playing a critical role in defending against DDoS attacks and unauthorized access attempts.
9 – Request Size Limit Policy
This policy caps the size of payloads sent to the API gateway, ensuring that requests exceeding a predetermined threshold are automatically rejected. By limiting request sizes, the policy is instrumental in preventing security vulnerabilities like buffer overflow attacks and ensuring efficient API traffic management.
10 – Cross-Origin Resource Sharing (CORS) Restriction Policy
The CORS Restriction policy allows API developers to specify appropriate headers for cross-domain requests, ensuring they are not blocked by browsers. This is crucial for maintaining the functionality and security of web applications that rely on APIs from different domains.
11 – Client Throttling Policy
This policy limits the number of API calls a consumer can make within a specified timeframe, rejecting requests that exceed the set limit. Such metered access is vital for managing API traffic, preventing overloading of the API gateway, and maintaining optimal service levels for all API consumers.
12 – Request Transformer Policy
The Request Transformer policy enables API developers to modify requests before they proceed further. This includes adding, replacing, or removing parts of the header under specific conditions, thus enhancing the flexibility and security of API interactions.
Optimizing API Security with SnapLogic
The SnapLogic API Management solution offers a robust policy hierarchy feature, essential for creating a secure and flexible API ecosystem. Policies can be meticulously applied at various levels – from the organizational level down to individual API versions, facilitating granular control over API security. This flexibility enables API administrators to implement foundational security measures like rate limiting and IP restrictions across all APIs within an organization or a project. For instance, a global client throttling policy plays a crucial role in preventing DDoS attacks by ensuring no single API consumer can overwhelm the Snaplex with excessive API requests.
Additionally, the ability to differentiate policies across various API versions allows for tailored application security, enhancing both the governance layer and the user experience. This approach is particularly effective in managing the lifecycle of APIs, ensuring that each version adheres to the latest security standards and best practices, such as OWASP guidelines for web application security and the prevention of vulnerabilities like SQL injection and data breaches.
We hope this overview has illuminated the array of security policies available in the SnapLogic API Management solution, designed to protect sensitive data, manage API traffic, and mitigate security risks. These policies, including OAuth authentication, SSL/TLS encryption, and API keys management, are pivotal for safeguarding your web applications, IoT devices, and REST APIs against an ever-evolving array of security threats.
Stay tuned for more insights into how our API management solution can empower API developers and consumers to efficiently bring API products to market, leveraging automation, real-time data processing, and secure API calls. If you’re eager to see these features in action and understand how they can enhance your API strategy, particularly in a DevOps environment, we invite you to request a demo of our API Management solution today. Experience firsthand how SnapLogic can fortify your APIs against the complex landscape of API security challenges.